What Is Tokenization Key Management Securityfirstcorp Com

Tokenization For Improved Data Security Key Applications And Use Cases What is tokenization key management? in this informative video, we will discuss the importance of tokenization key management in the realm of data security. In data security, tokenization is the process of converting sensitive data into a nonsensitive digital replacement, called a token, that maps back to the original. tokenization can help protect sensitive information. for example, sensitive data can be mapped to a token and placed in a digital vault for secure storage.
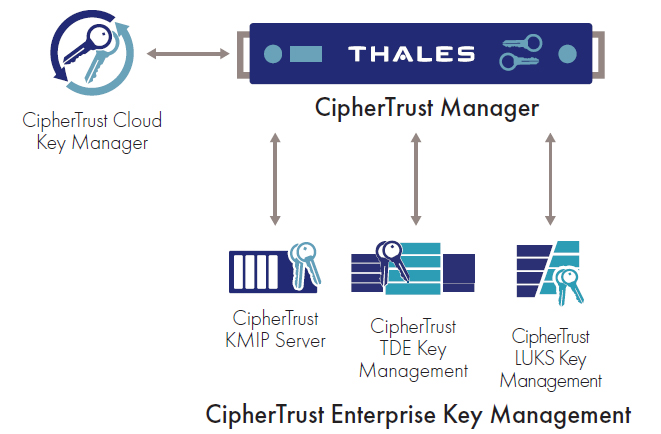
Enterprise Key Management Protect sensitive data with tokenization. learn how data tokenization works, its benefits, real world examples, and how to implement it for security and compliance. What is tokenization? tokenization protects sensitive data by substituting non sensitive data. tokenization creates an unrecognizable tokenized form of the data that maintains the format of the source data. Effective key management is essential to maintain the security of encrypted data and prevent unauthorized access. in contrast, tokenization reduces the complexity of key management, as the token vault is the primary component that requires secure management. Key management cheat sheet introduction this key management cheat sheet provides developers with guidance for implementation of cryptographic key management within an application in a secure manner. it is important to document and harmonize rules and practices for: key life cycle management (generation, distribution, destruction) key compromise, recovery and zeroization key storage key.
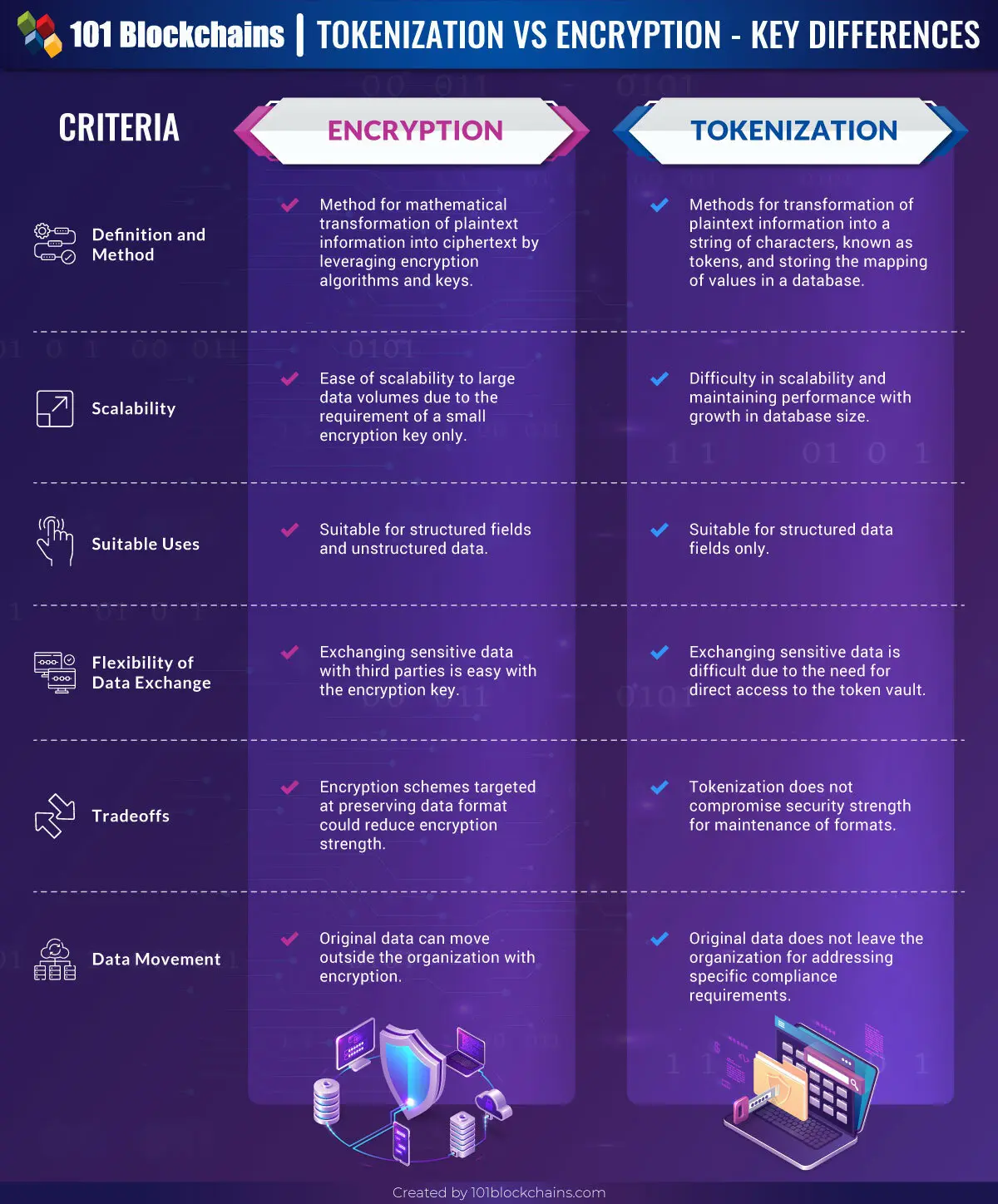
Tokenization Vs Encryption Key Differences 101 Blockchains Effective key management is essential to maintain the security of encrypted data and prevent unauthorized access. in contrast, tokenization reduces the complexity of key management, as the token vault is the primary component that requires secure management. Key management cheat sheet introduction this key management cheat sheet provides developers with guidance for implementation of cryptographic key management within an application in a secure manner. it is important to document and harmonize rules and practices for: key life cycle management (generation, distribution, destruction) key compromise, recovery and zeroization key storage key. Tokenization is an effective strategy for securing sensitive data by replacing it with non sensitive tokens. it provides strong data security and helps reduce compliance scope by restricting access to sensitive information. Tokenization serves as a vital mechanism for protecting sensitive data in the realm of cyber security. by replacing confidential information with tokens, organizations can bolster their data security defenses and maintain compliance with regulatory standards. Data tokenization is a security method for replacing sensitive data with non sensitive, unique tokens. the original data is stored securely in a separate database, and the tokens are used in its place for processing or analytics. In this comprehensive guide, we will explore the meaning of tokenization, its significance in various industries, its key principles and benefits, and how it works to safeguard sensitive information.

Key Management Service Cloud Product Samsung Sds India Tokenization is an effective strategy for securing sensitive data by replacing it with non sensitive tokens. it provides strong data security and helps reduce compliance scope by restricting access to sensitive information. Tokenization serves as a vital mechanism for protecting sensitive data in the realm of cyber security. by replacing confidential information with tokens, organizations can bolster their data security defenses and maintain compliance with regulatory standards. Data tokenization is a security method for replacing sensitive data with non sensitive, unique tokens. the original data is stored securely in a separate database, and the tokens are used in its place for processing or analytics. In this comprehensive guide, we will explore the meaning of tokenization, its significance in various industries, its key principles and benefits, and how it works to safeguard sensitive information.
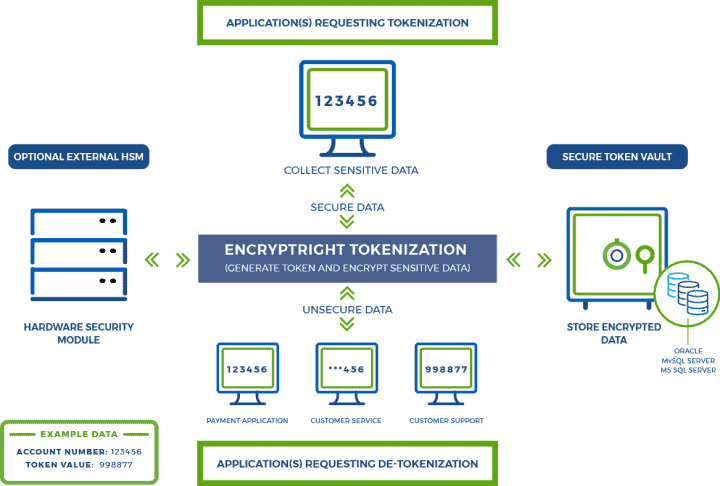
Tokenization Software Solution Encryptright Prime Factors Data tokenization is a security method for replacing sensitive data with non sensitive, unique tokens. the original data is stored securely in a separate database, and the tokens are used in its place for processing or analytics. In this comprehensive guide, we will explore the meaning of tokenization, its significance in various industries, its key principles and benefits, and how it works to safeguard sensitive information.
Comments are closed.