Tokenization For Improved Data Security Overview Of Security

Tokenization For Improved Data Security Overview Of Security Security sensitive applications use tokenization to replace sensitive data, such as personally identifiable information (pii) or protected health information (phi), with tokens to reduce security risks. The security and risk reduction benefits of tokenization require that the tokenization system is logically isolated and segmented from data processing systems and applications that previously processed or stored sensitive data replaced by tokens.
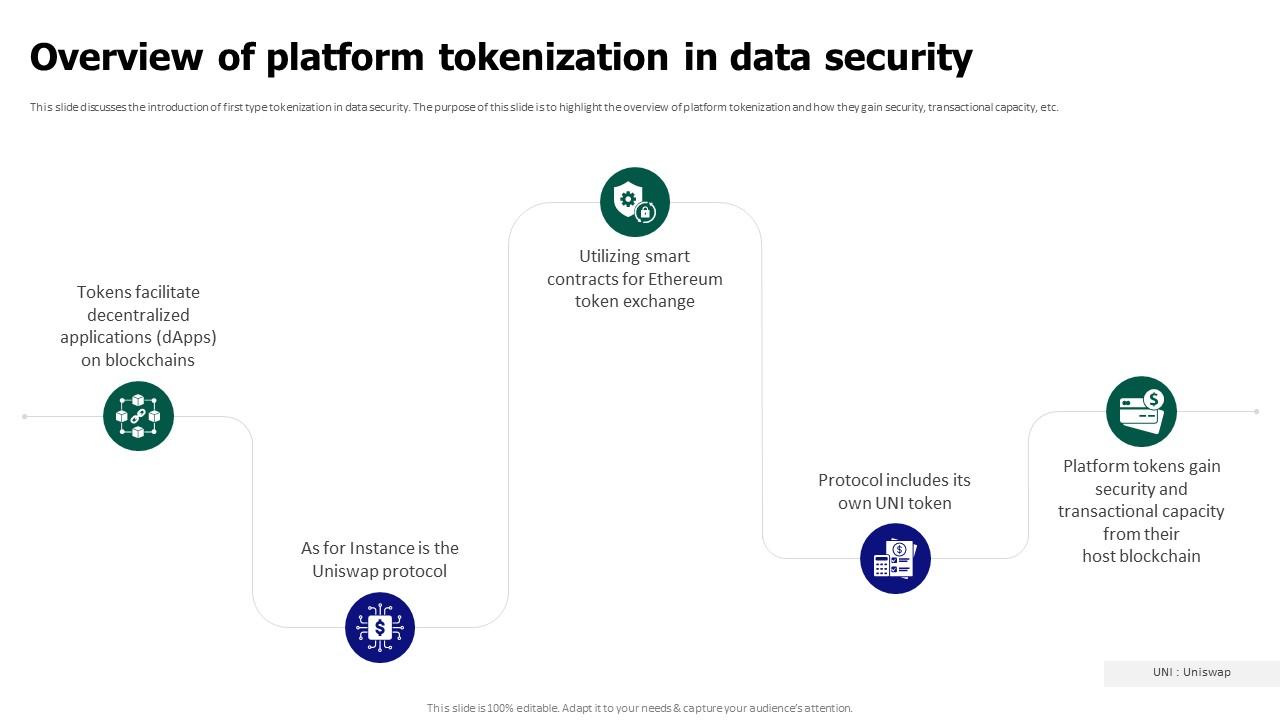
Tokenization For Improved Data Security Overview Of Platform As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. Tokenization security is a crucial aspect of protecting sensitive data in today’s digital landscape. it involves replacing sensitive information, such as credit card numbers or personal identifiable information (pii), with a unique, randomly generated token. Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens,. Tokenization, as a data security technique, offers a powerful solution to this challenge. by replacing sensitive data with non sensitive tokens, tokenization ensures that even if the tokens are compromised, the original data remains protected and inaccessible.
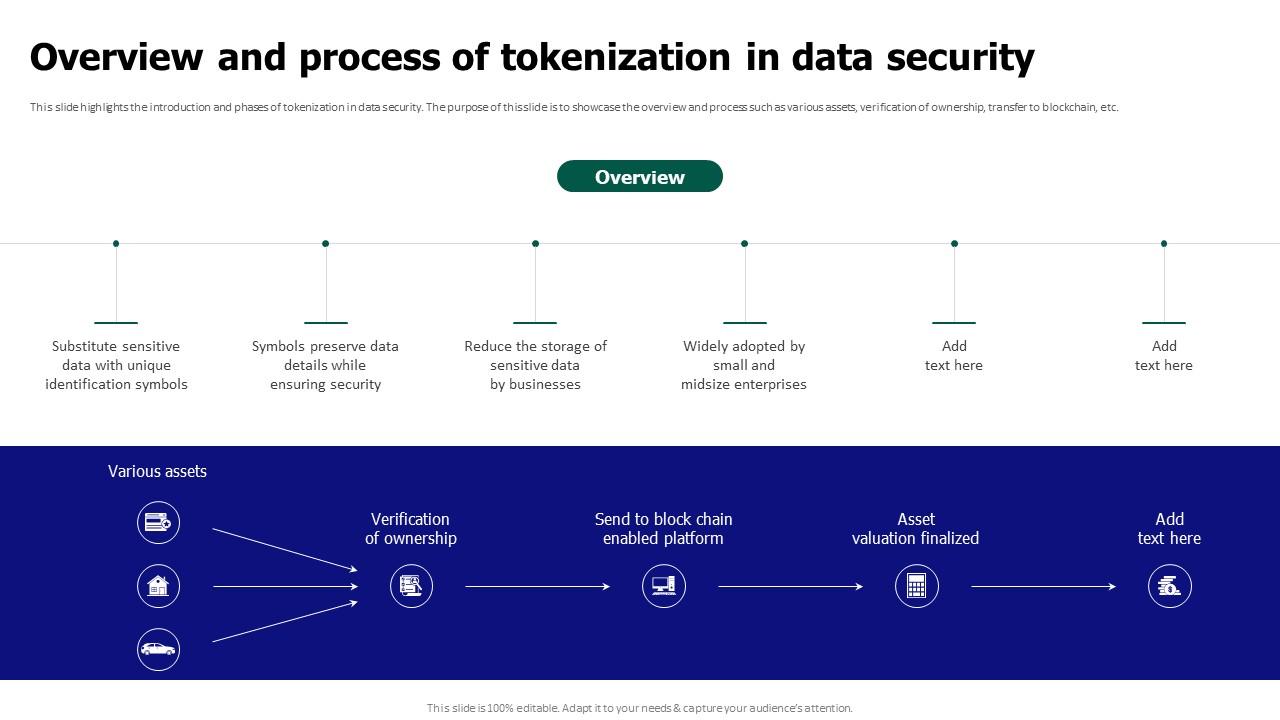
Tokenization For Improved Data Security Overview And Process Of Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens,. Tokenization, as a data security technique, offers a powerful solution to this challenge. by replacing sensitive data with non sensitive tokens, tokenization ensures that even if the tokens are compromised, the original data remains protected and inaccessible. In this article, we will break down how data tokenization works, explore its key benefits over traditional security measures, and examine why it has become an essential component of modern cybersecurity strategies. Data tokenization is like giving your valuable stuff a secret code. you take sensitive data, such as credit card numbers or social security numbers, and swap them out with random, harmless looking data called tokens. these tokens look like real data, but they are useless to hackers because they don’t represent the actual information. This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods. Explore the essentials of data tokenization, its impact on data security and privacy, and how businesses can leverage it for safeguarding sensitive information.

Tokenization For Improved Data Security Main Data Security Tokenization In this article, we will break down how data tokenization works, explore its key benefits over traditional security measures, and examine why it has become an essential component of modern cybersecurity strategies. Data tokenization is like giving your valuable stuff a secret code. you take sensitive data, such as credit card numbers or social security numbers, and swap them out with random, harmless looking data called tokens. these tokens look like real data, but they are useless to hackers because they don’t represent the actual information. This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods. Explore the essentials of data tokenization, its impact on data security and privacy, and how businesses can leverage it for safeguarding sensitive information.

An Overview Of Tokenization In Data Security This comprehensive article delves into the critical role of tokenization in modern data security, exploring its core concepts, operational mechanisms, and distinct advantages over traditional encryption methods. Explore the essentials of data tokenization, its impact on data security and privacy, and how businesses can leverage it for safeguarding sensitive information.
Comments are closed.