Tokenization For Improved Data Security Overview And Process Of
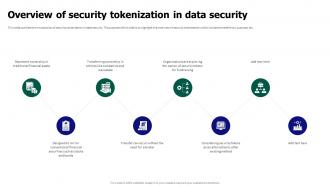
Tokenization For Improved Data Security Overview Of Security Industries subject to financial, data security, regulatory, or privacy compliance standards are increasingly looking for tokenization solutions to minimize distribution of sensitive data, reduce risk of exposure, improve security posture, and alleviate compliance obligations. Tokenization, when applied to data security, is the process of substituting a sensitive data element with a non sensitive equivalent, referred to as a token, that has no intrinsic or exploitable meaning or value.

Tokenization For Improved Data Security Main Data Security Tokenization Data tokenization is a data security process that replaces sensitive data with a non sensitive value, called a token. tokens can be random numbers, strings of characters, or any other non identifiable value. when sensitive data is tokenized, the original data is stored securely in a token vault. At its core, tokenization is the process of exchanging sensitive data for non sensitive data called tokens. these tokens retain certain elements of the original data, such as length and format, but are undecipherable and irreversible. As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. As we delve deeper into the concept of tokenization in data security, we will explore its process, benefits, and the differences between tokenization and encryption.
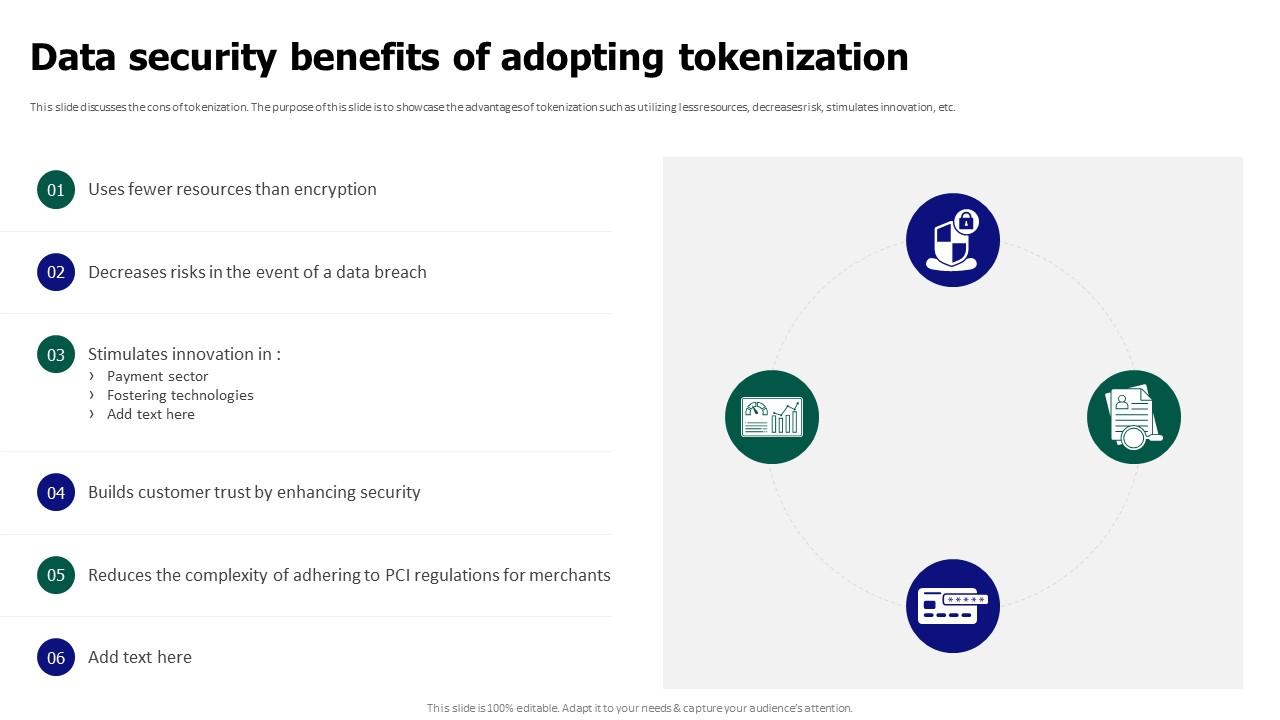
Tokenization For Improved Data Security Data Security Benefits Of As businesses navigate an increasingly challenging and complex web of privacy regulations, data tokenization – a method that replaces sensitive data with non sensitive placeholders, offering enhanced security without compromising usability – looks set to be the future of digital security. As we delve deeper into the concept of tokenization in data security, we will explore its process, benefits, and the differences between tokenization and encryption. Understand the process of tokenization, its significance in data security, and how it protects sensitive information by replacing it with non sensitive equivalents. learn about different tokenization methods, applications, and best practices for implementation. Data tokenization is a technique used in data security to protect sensitive data by replacing it with a unique identifier or token. the token is then used in place of the original data in order to perform transactions or other operations, while the original data remains protected. In this article, we will break down how data tokenization works, explore its key benefits over traditional security measures, and examine why it has become an essential component of modern cybersecurity strategies. Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens,.
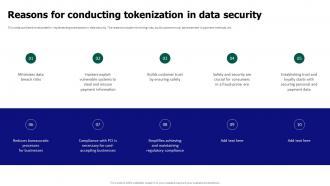
Tokenization For Improved Data Security Reasons For Conducting Understand the process of tokenization, its significance in data security, and how it protects sensitive information by replacing it with non sensitive equivalents. learn about different tokenization methods, applications, and best practices for implementation. Data tokenization is a technique used in data security to protect sensitive data by replacing it with a unique identifier or token. the token is then used in place of the original data in order to perform transactions or other operations, while the original data remains protected. In this article, we will break down how data tokenization works, explore its key benefits over traditional security measures, and examine why it has become an essential component of modern cybersecurity strategies. Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens,.

Tokenization For Improved Data Security Characteristics Of Utility In this article, we will break down how data tokenization works, explore its key benefits over traditional security measures, and examine why it has become an essential component of modern cybersecurity strategies. Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens,.
Comments are closed.