Tokenization For Improved Data Security Different Phases Of

Tokenization For Improved Data Security Different Phases Of Industries subject to financial, data security, regulatory, or privacy compliance standards are increasingly looking for tokenization solutions to minimize distribution of sensitive data, reduce risk of exposure, improve security posture, and alleviate compliance obligations. Discover how we guide you through implementing tokenization best practices, avoiding common missteps to ensure secure data protection.

Tokenization For Improved Data Security Main Data Security Tokenization Tokenization, when applied to data security, is the process of substituting a sensitive data element with a non sensitive equivalent, referred to as a token, that has no intrinsic or exploitable meaning or value. Learn how to implement tokenization to protect sensitive data and enhance your system's security. this guide covers the tokenization process, benefits, and best practices. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. you must be logged in to download this presentation. we’ll check if you have an account, and help create one if you don’t. please enter your email address below to receive a password reset link. Learn how data tokenization works, its benefits, real world examples, and how to implement it for security and compliance. with data breaches on the rise and regulations tightening across industries, protecting sensitive information has never been more critical.
Tokenization For Improved Data Security Overview Of Security The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. you must be logged in to download this presentation. we’ll check if you have an account, and help create one if you don’t. please enter your email address below to receive a password reset link. Learn how data tokenization works, its benefits, real world examples, and how to implement it for security and compliance. with data breaches on the rise and regulations tightening across industries, protecting sensitive information has never been more critical. Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens, helping. Understand the process of tokenization, its significance in data security, and how it protects sensitive information by replacing it with non sensitive equivalents. learn about different tokenization methods, applications, and best practices for implementation. Tokenization is the process of hiding the contents of a dataset by replacing sensitive or private elements with a series of non sensitive, randomly generated elements (called a token). tokenization is gaining popularity for data security purposes in business intelligence, fintech, and ecommerce sectors, among others. throughout the process, the link between the token and real values cannot be. Data tokenization is a crucial technique in ensuring the security and privacy of sensitive information. in this comprehensive guide, we will dive deep into the world of data tokenization, uncovering its definition, importance, various types, implementation strategies, and future trends.
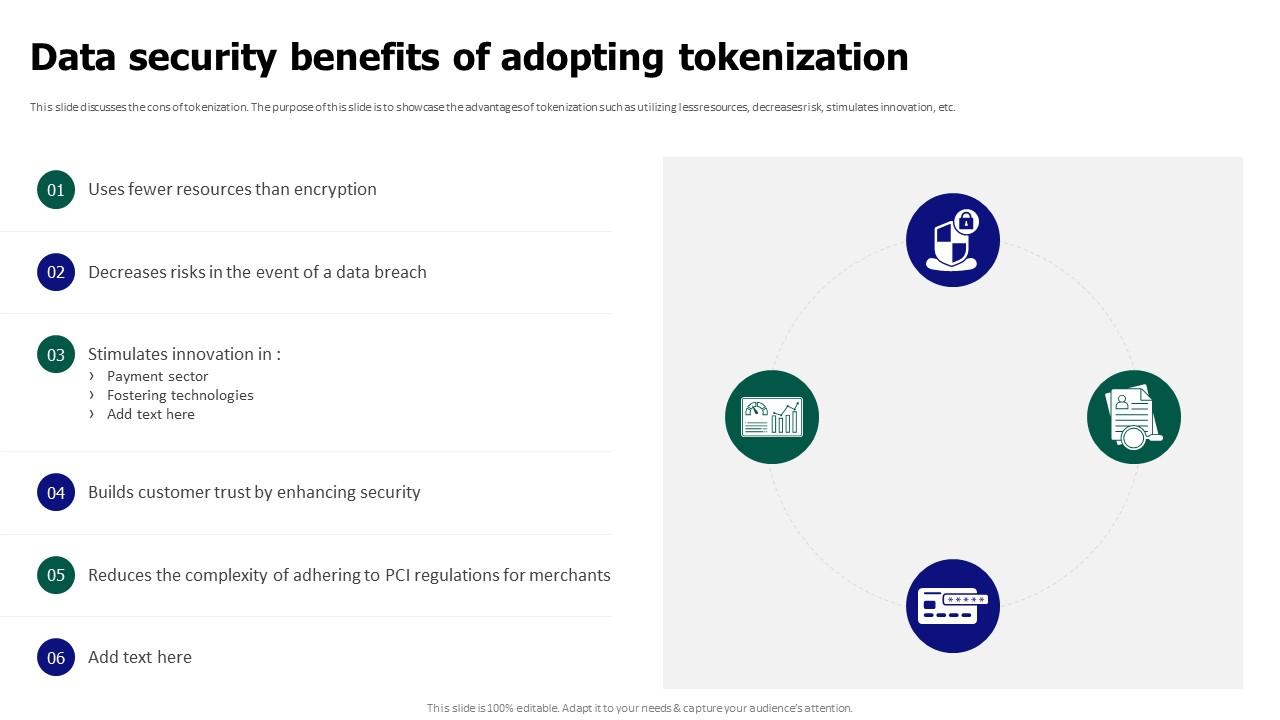
Tokenization For Improved Data Security Data Security Benefits Of Among the data protection techniques available, tokenization is a powerful method for protecting sensitive information. tokenization replaces real data with format preserving tokens, helping. Understand the process of tokenization, its significance in data security, and how it protects sensitive information by replacing it with non sensitive equivalents. learn about different tokenization methods, applications, and best practices for implementation. Tokenization is the process of hiding the contents of a dataset by replacing sensitive or private elements with a series of non sensitive, randomly generated elements (called a token). tokenization is gaining popularity for data security purposes in business intelligence, fintech, and ecommerce sectors, among others. throughout the process, the link between the token and real values cannot be. Data tokenization is a crucial technique in ensuring the security and privacy of sensitive information. in this comprehensive guide, we will dive deep into the world of data tokenization, uncovering its definition, importance, various types, implementation strategies, and future trends.
Tokenization For Improved Data Security Reasons For Conducting Tokenization is the process of hiding the contents of a dataset by replacing sensitive or private elements with a series of non sensitive, randomly generated elements (called a token). tokenization is gaining popularity for data security purposes in business intelligence, fintech, and ecommerce sectors, among others. throughout the process, the link between the token and real values cannot be. Data tokenization is a crucial technique in ensuring the security and privacy of sensitive information. in this comprehensive guide, we will dive deep into the world of data tokenization, uncovering its definition, importance, various types, implementation strategies, and future trends.
Comments are closed.