Implementing Effective Tokenization Steps To Implement Security

Implementing Effective Tokenization Steps To Implement Security Discover how we guide you through implementing tokenization best practices, avoiding common missteps to ensure secure data protection. Learn how to implement tokenization to protect sensitive data and enhance your system's security. this guide covers the tokenization process, benefits, and best practices.

Implementing Effective Tokenization Steps For Implementing Asset Tokenization is the process of replacing actual sensitive data elements with non sensitive data elements that have no exploitable value for data security purposes. Implementing data tokenization is a highly effective method to ensure secure big data storage. by replacing sensitive information with unique tokens, organizations can significantly mitigate the risks associated with data breaches and unauthorized access. The digital landscape is a battlefield where data security is the ultimate prize. in this arena, tokenization emerges as a formidable shield, transforming sensitive information into an unintelligible, non sensitive equivalent – a token. but the mere act of tokenizing isn’t enough. By following the best practices outlined in this article, organizations can ensure a successful tokenization implementation that meets their security and compliance requirements.
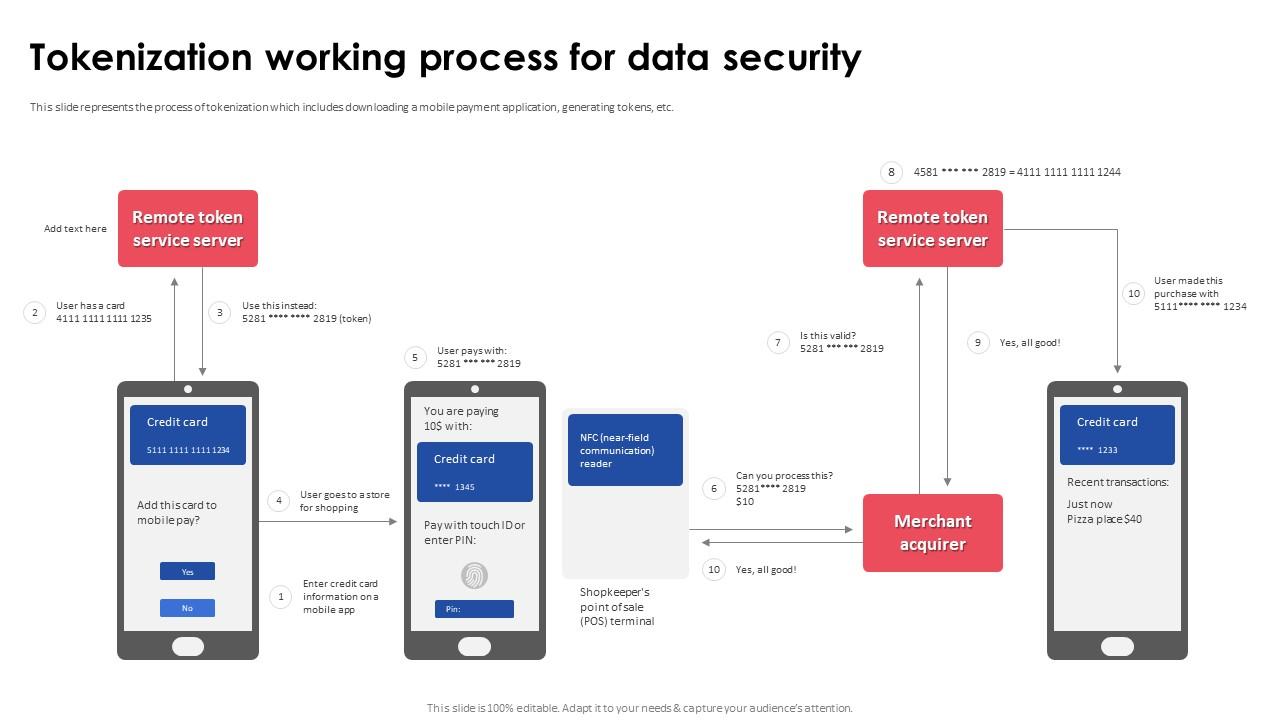
Tokenization Working Process For Data Security Implementing Effective The digital landscape is a battlefield where data security is the ultimate prize. in this arena, tokenization emerges as a formidable shield, transforming sensitive information into an unintelligible, non sensitive equivalent – a token. but the mere act of tokenizing isn’t enough. By following the best practices outlined in this article, organizations can ensure a successful tokenization implementation that meets their security and compliance requirements. In this comprehensive guide, we will dive deep into tokenization services, exploring the basics, the process, and the implementation. we will also discuss the future of tokenization and its impact on the financial industry, data privacy, and compliance. Implementing tokenization reduces regulatory scope and minimizes potential financial losses from data breaches, lowering overall costs. integrating tokenization into legacy systems can involve technical hurdles, compatibility checks, and significant planning. Implementing tokenization requires careful planning and consideration, but the benefits far outweigh the challenges. by following the steps outlined in this article, you can enhance your data security and protect your organization from potential threats. Implementing data tokenization is a strategic decision that significantly enhances data security and privacy for organizations. data tokenization helps protect sensitive information from unauthorized access, reducing the risk of data breaches.
Steps To Implement Security Tokenization Strategy Platform Tokenization In this comprehensive guide, we will dive deep into tokenization services, exploring the basics, the process, and the implementation. we will also discuss the future of tokenization and its impact on the financial industry, data privacy, and compliance. Implementing tokenization reduces regulatory scope and minimizes potential financial losses from data breaches, lowering overall costs. integrating tokenization into legacy systems can involve technical hurdles, compatibility checks, and significant planning. Implementing tokenization requires careful planning and consideration, but the benefits far outweigh the challenges. by following the steps outlined in this article, you can enhance your data security and protect your organization from potential threats. Implementing data tokenization is a strategic decision that significantly enhances data security and privacy for organizations. data tokenization helps protect sensitive information from unauthorized access, reducing the risk of data breaches.
Implementing Effective Tokenization Process Phases Of Implementing Implementing tokenization requires careful planning and consideration, but the benefits far outweigh the challenges. by following the steps outlined in this article, you can enhance your data security and protect your organization from potential threats. Implementing data tokenization is a strategic decision that significantly enhances data security and privacy for organizations. data tokenization helps protect sensitive information from unauthorized access, reducing the risk of data breaches.
Comments are closed.